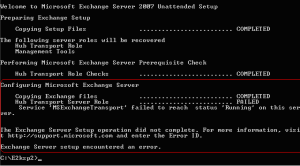
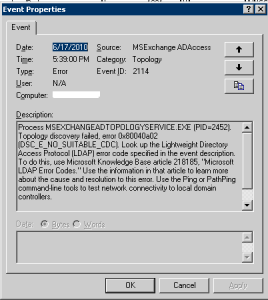
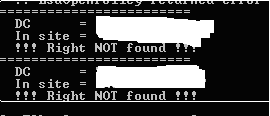
Here are the reference URLs to prior Blog entries of interest on this topic:
In this Blog entry I will analyze mailflow across the Routing Group Connector to provide a clearer picture of what occurs while Organizations are Transitioning from Exchange 2003 to Exchange 2007.
1. Let's begin by examining the 2 Servers that comprise the Exchange 2003 Site titled 'First Administrative Group', and, the 2 Servers in the Exchange 2007 Site titled 'Exchange Administrative Group'. We see 4 Servers total:
Exchange 2003
- S01-EX00
- S01-EX00-1
- S01-EX01
- S01-Ex02
2. The Exchange 2007 Servers have been introduced into the Exchange 2003 Organization named 'ITPS Lab Exchange Organization'. When this occurred, a Bi-Directional Routing Group Connector was generated as part of the installation process. We see here the Routing Group Connector titled 'ITPS Lab Interop RGC' (actually, this is a hand-generated Routing Group Connector I created 'after the fact'). In this example, the Exchange 2007 Installation Process generated the RGC, then I generated an additional RGC and finally, deleted the RGC created automatically by the Exchange 2007 Installation Process. In a typical environment, we would generate (with the Exchange 2007 Installation Process) and maintain a single Routing Group Connector (RGC). Unless of course multiple Exchange 2007 Hub Transport Role Servers are required.
3. Let's examine the Properties of the Exchange 2003 Routing Group Connector.
4. Here we see the Exchange 2003 Server (titled S01-EX00) is the Default Server used for Routing Messages over the Routing Group Connector to the Exchange 2007 Remote Bridghead Servers.
5. The Exchange 2007 Server that is the Remote Bridgehead Server for this Exchange 2003 Routing Group Connector is titled 'S01-EX01'. It is an Exchange 2007 Hub Transport Role Server running Exchange 2007.
6. Now, let's examine the Routing Group Connector Properties for the Exchange 2007 Routing Group. Remember, Exchange 2007 only uses Routing Group Connectors for interoperability 'backwards' to Exchange 2003 Organizations.
7. Again, we see reciprocity! The Exchange 2007 Hub Transport Role Server (titled 'S01-EX001') 'connects' over this Routing Group Connector to the Exchange 2003 Server (titled in the next caption as 'S01-EX00').
8. The Remote Bridgehead Server for the Exchange 2003 Routing Group is identified as 'S01-EX00'.
9. Next I move to the Exchange 2007 Hub Transport Role Server titled 'S01-EX01'. As you can see, through the Exchange Management Console there is no Graphical Interface for Administering a Routing Group Connector (RGC). We will instead use the Exchange Management Shell to invoke the 'Get-RoutingGroupConnector' Commandlet.
10. Initially, when I offer the Exchange Management Shell Commandlet 'Get-RoutingGroupConnector' we see data listed in a Table from the default feedback. Here's the Exchange Management Shell Commandlet:
get-routinggroupconnector
11. Next, to see the full detail for this EMS Commandlet I issue the following Commandlet using the 'Pipeline Parameter' (|) followed by 'Format List' (fl):
get-routinggroupconnector | fl
12. The second half of the EMS window appears here. Notice we have rich granularity in the Attributes available.
13. So, what do we have here? This is another variation of the EMS Commandlet denoting additionall Attributes be displayed. Here we can see both 'Source Transport Server' and 'Target Transport Server' by using the followng EMS Commandlet variation:
get-routinggroupconnector |fl targetroutinggroup,targettransportservers,sourcetransportservers
14. Next I add the 'Cost' Attribute to display in this EMS Commandlet. Here's the Commandlet syntax:
get-routinggroupconnector |fl targetroutinggroup,targettransportservers,sourcetransportservers,cost
15. Finally, I personally favor the following EMS Commandlet Syntax for this Commandlet. It allows me to keep track of versional changes.
get-routinggroupconnector |fl targetroutinggroup,targettransportservers,sourcetransportservers,cost,whencreated,whenchanged
16. Okay, so where are we? We just spent time using the Exchange Management Shell (EMS) to analyze the output of the Routing Group Connector that links the Legacy Exchange 2003 Organization to the initial Exchange 2007 Hub Transport Role Server in our Messaging Environment. We are reviewing these configuration details to understand how and where SMTP Messages 'Route' in a Transitional Strategy that involves Exchange 2003 and Exchange 2007.
17. Next, I would like to review the 'Routing Log Viewer' available from within the Exchange Management Console in Exchange 2007. You will find it on the 'Tools' leaf of the Exchange 2007 Management Console.
18. The 'Routing Log Viewer' in the Exchange 2007 Management Console (EMC) provide XML Files that 'record' the Routing Configuratin across all Routing Group Connectors, Send Connectors and Receive Connectors. Foreign Connectors are not included in the Routing Log Viewer as Foreign Connectors simply 'pickup' SMTP Messages from the 'Pickup' Directory.
19. I select the most recent XML File to examine the contents.
20. Most Exchange System Engineer's have never seen, nor used the Routing Log Viewer. Here we can see the Active Directory Site whereby the Exchange 2007 Servers are visible. And, the Exchange 2003 Routing Group where the Exchange 2003 Servers are visible.
21. Upon moving to the 'Servers' Tab in the Routing Log Viewer we see a more detailed breakdown of both Exchange 2003 and Exchange 2007 Servers. Note the Exchange 2007 Servers use the Active Diretory Sites as their respective 'Routing Boundaries' (lower portion of capture) while the Exchange 2003 Servers use the Routing Group as their respective 'Routing Boundaries'.
22. Next we observe the 'Send Connectors' Tab of the Routing Log Viewer. Some of the details of the Routing Group Connector are present in this Graphical Interface.
23. As part of the endeavor to understand SMTP Message Routing across a Routing Group Connector I would like to 'follow' a message from an Exchange 2007 User Mailbox, across the Routing Group Connector to an Exchange 2003 User Mailbox. We can use Message Tracking available in the Exchange 2003 System Manager (ESM) and in the Exchange 2007 Management Console (EMC). Here I begin logging in as an Exchange 2007 Mailbox User fictitiously named 'Steve Railson' to send e-mail to an Exchange 2003 Mailbox User named 'Field1'.
24. Logging in to prepare e-mail for an Exchange 2003 Target (from an Exchange 2007 Mailbox User).
25. E-mail prepared and sent. This message should 'travel across' the Exchange 2007 Hub Transport Role Server to the Routing Group Connector (RGC), ultimately to the Exchange 2003 Routing Group Server and finally to the destination Exchange 2003 User Mailbox Server. Let's follow it's path!
26. Confirmation of the 'CC' of this message from/to himself.
27. I move to the Exchange 2003 Mailbox Server Role titled 'S01-EX00-1' to confirm an Exchange 2003 Mailbox User named 'Field1'. Confirmation complete! Our Mailbox is on this server!
28. When I open the 'Messaging Tracking Center' in Exchange 2003 and input query parameters (like Exchange 2007 Mailbox User Name, Mailbox Server Name, etc.) the response is identification of the exact message sent. Next, let's look a the Message Tracking in the Exchange 2007 Messaging Tracking to determine how this SMTP Message 'travelled' using which Connector (it should be our Routing Group Connector!).
29. I move to the EMC on an Exchange 2007 Hub Transport Role Server. Next, I open the Message Tracking Application.
30. When I input a narrow time range (the exact 5 minute interval I know the message was sent) I receive a response with the exact message tracking detail. Now, here is our point of confirmation - will the SMTP Message from the Exchange 2007 Mailbox User (srailson User ID) transmit over the Routing Group Connector as we expect? Let's see.
31. Yes! Success! A closer examination of the 'ConnectorID' Attribute and we see 'Intra-Organization SMTP Send Connector' indicated as the Connector used to transmit this SMTP Message from the Exchange 2007 Hub Transport Role to the Exchange 2003 Routing Group Server. Thus providing 'mailflow' between a Legacy Exchange 2003 Organization and new Exchange 2007 Hub Transport Role Servers in the same Exchange Organization.
In this Blog entry I review many of the configuration parameters of an Exchange 2007 Routing Group Connector. I use the many of the Exchange 2007 Applications for analysi, including the Exchange Management Shell Commandlet 'get-routinggroupconnector', the Exchange Management Console, the Routing Log Viewer and Message Tracking. While, when working on the Exchange 2003 Server Role I use the Exchange System Manager and the Message Tracking Center. All of these Tools prove useful when determining the SMTP Message Routing in a joint Exchange 2003 and Exchange 2007 Messaging Infrastructure!